Inter-Process Communication In Linux
This beginner-friendly guide walks you through TCP, UDP, and Unix domain sockets, tools like ss and netstat, and real-world pentesting scenarios to detect suspicious activity. Includes a quiz to test your knowledge and sharpen your skills.
1. Introduction to Inter-Process Communication (IPC)
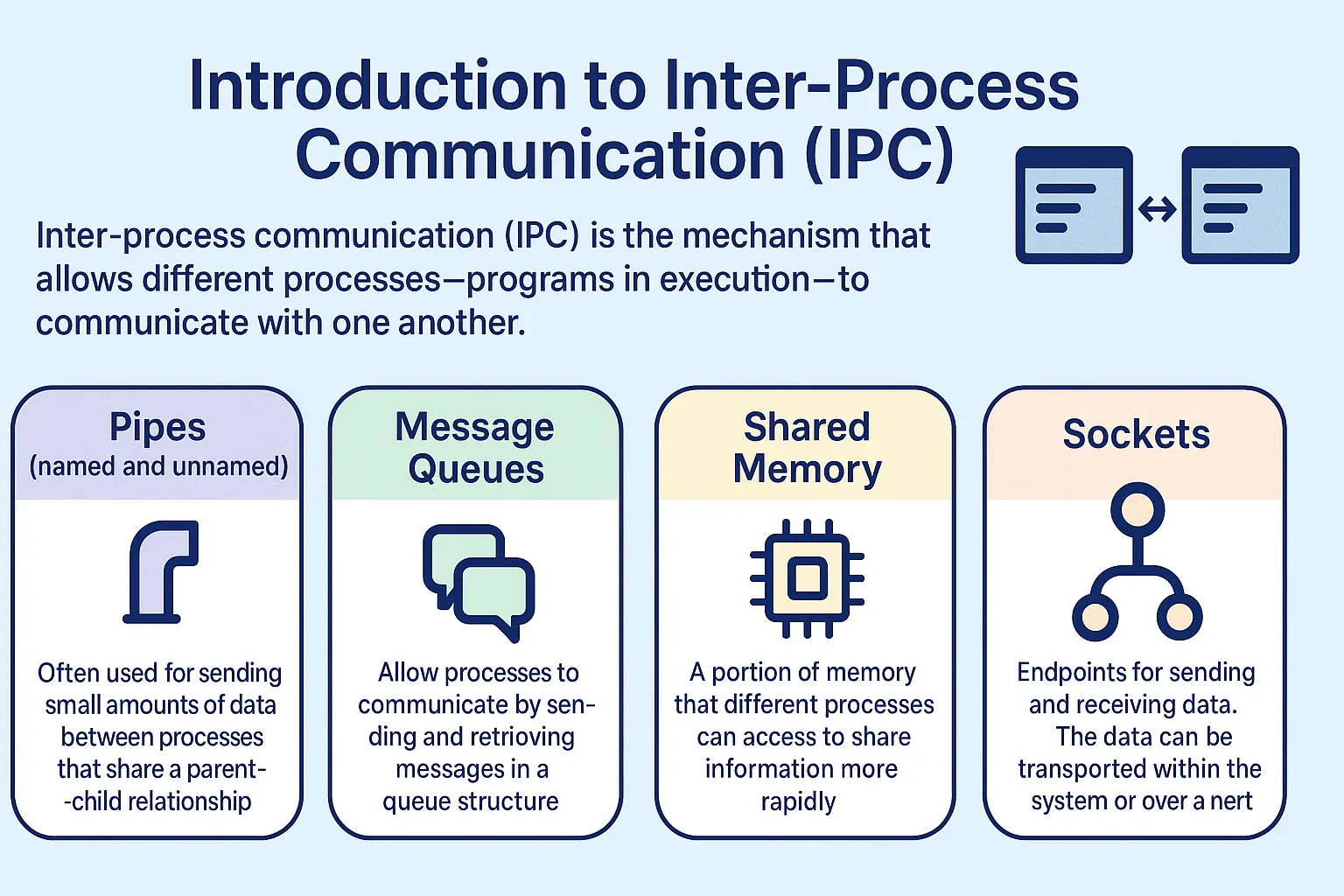
Inter-process communication (IPC) is the mechanism that allows different processes—programs in execution—to communicate with one another. In Linux, IPC can be facilitated by several methods:
-
Pipes (named and unnamed): Often used for sending small amounts of data between processes that share a parent-child relationship.
-
Message Queues: Allow processes to communicate by sending and retrieving messages in a queue structure.
-
Shared Memory: A portion of memory that different processes can access to share information more rapidly.
-
Sockets: Endpoints for sending and receiving data. The data can be transported within the same system or over a network.
For pentesters, understanding IPC is critical. Attackers and defenders alike need to know where data is flowing, how processes talk to each other, and whether any part of that communication can be intercepted or manipulated.
2. Sockets in Linux
The socket abstraction in Linux (and in most other modern operating systems) provides a universal interface for communication between processes. A socket represents one endpoint of a two-way communication link. When two processes exchange data, one will typically act as a server (listening socket) and the other as a client (connecting socket).
2.1 TCP Sockets
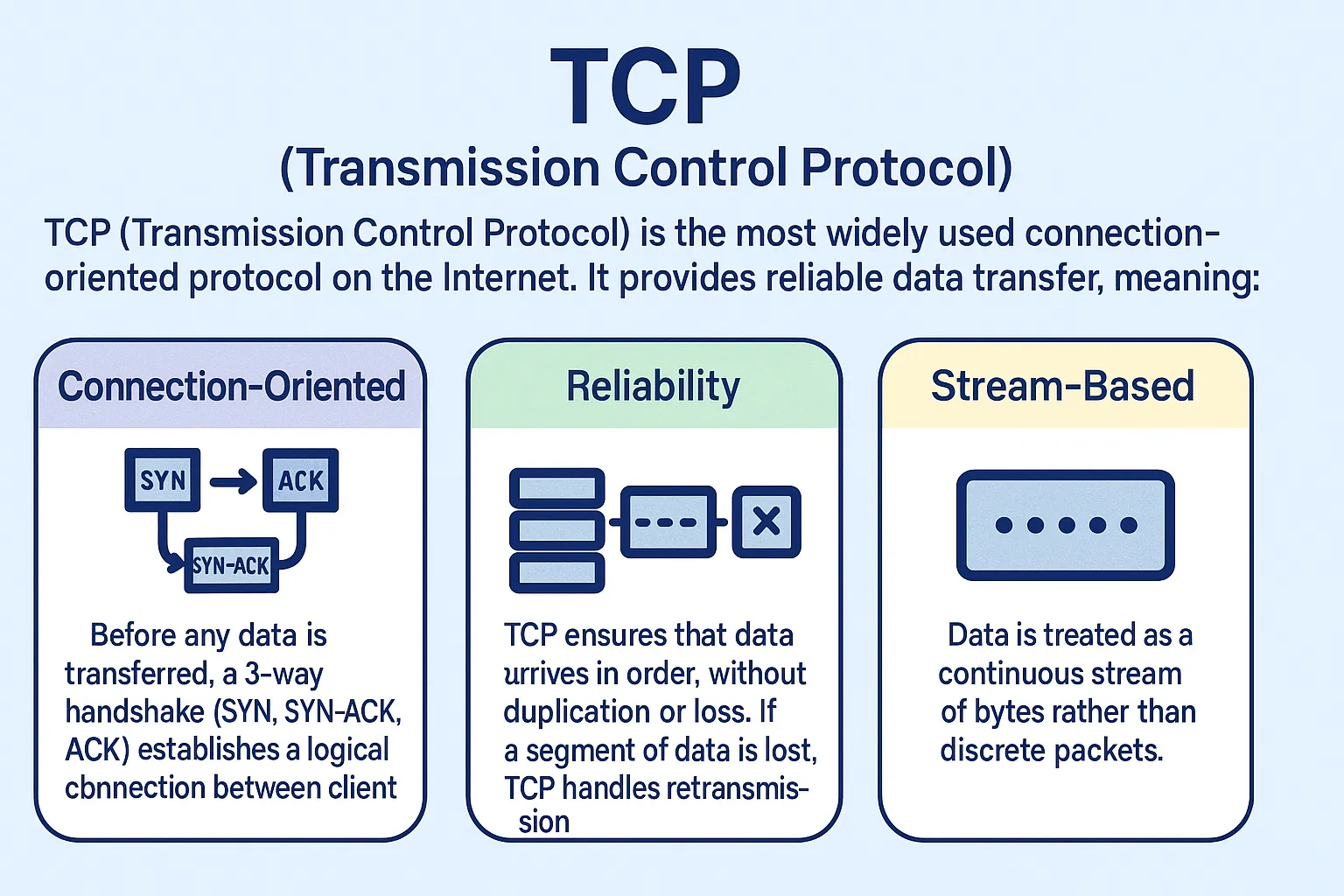
TCP (Transmission Control Protocol) is the most widely used connection-oriented protocol on the Internet. It provides reliable data transfer, meaning:
-
Connection-Oriented: Before any data is transferred, a 3-way handshake (SYN, SYN-ACK, ACK) establishes a logical connection between the client and server.
-
Reliability: TCP ensures that data arrives in order, without duplication or loss. If a segment of data is lost, TCP handles retransmission.
-
Stream-Based: Data is treated as a continuous stream of bytes rather than discrete packets.
In typical Linux usage:
-
A server process creates a socket, binds it to an IP address and port, and listens for incoming connections.
-
A client process connects to that IP and port, thus establishing a dedicated communication channel.
-
TCP is used for applications where data accuracy and order are more critical than speed or overhead (e.g., SSH, HTTP, HTTPS).
From a pentesting perspective:
-
TCP is often a prime target for port scanning (Nmap, for instance) and for advanced methods like banner grabbing.
-
Because it’s so widely used, vulnerabilities often exist in the software or services listening on these TCP ports.
2.2 UDP Sockets
UDP (User Datagram Protocol) is a connectionless protocol. Key features include:
-
Connectionless: There is no formal handshake. The sender simply sends data to a recipient’s IP and port. The receiver may or may not be ready to accept it.
-
No Guaranteed Delivery: Data can be lost, duplicated, or arrive out of order. There’s no built-in mechanism for retransmission.
-
Speed Over Reliability: Without the overhead of maintaining a connection or sequence numbers, UDP is typically faster for real-time or low-latency requirements.
Commonly used by:
- DNS, VoIP (Voice over IP) applications, streaming services, gaming services, and SNMP (Simple Network Management Protocol).
For pentesters:
-
UDP can sometimes be overlooked in security audits, but can be equally dangerous if misconfigured.
-
Testing often involves checking if DNS or other UDP-based services are vulnerable to reflection or amplification attacks.
2.3 Unix Domain Sockets
While TCP/UDP sockets can be used for communication over networks (including loopback addresses for local-only communication), Unix domain sockets are used exclusively for communication within the same host.
-
They operate through the file system namespace (i.e., they can be represented as a file in
/tmpor/var/run, among other locations). -
Unix domain sockets are faster than TCP/UDP because they do not require network-layer overhead when processes communicate on the same machine.
-
Many local services (e.g., MySQL, Docker Engine, system daemons) use Unix domain sockets for more secure, high-speed local communications.
For pentesters:
-
Sometimes you need to check if a service binds only to Unix domain sockets for local use. This could be a privilege escalation path if you can inject traffic or manipulate these sockets.
-
Tools like
socatornc(netcat) can sometimes be used to interact with Unix domain sockets if you have local access.
3. Observing Socket Usage
Knowing how to observe which processes use which sockets is a vital skill. This is especially important when you suspect malicious activity or during a pentest when you want to map out the services running on a compromised machine.
3.1 Tools (netstat / ss)
Traditionally, netstat was used for listing open ports, connections, and network statistics. However, modern Linux distributions often encourage using ss (socket statistics). Both serve a similar purpose:
-
netstat -anp-
-a: Show all listening and non-listening sockets. -
-n: Show numerical addresses instead of trying to resolve hostnames. -
-p: Show the PID (Process ID) and name of the program to which the socket belongs.
-
Example usage:
# Using netstat
netstat -anp | grep LISTEN 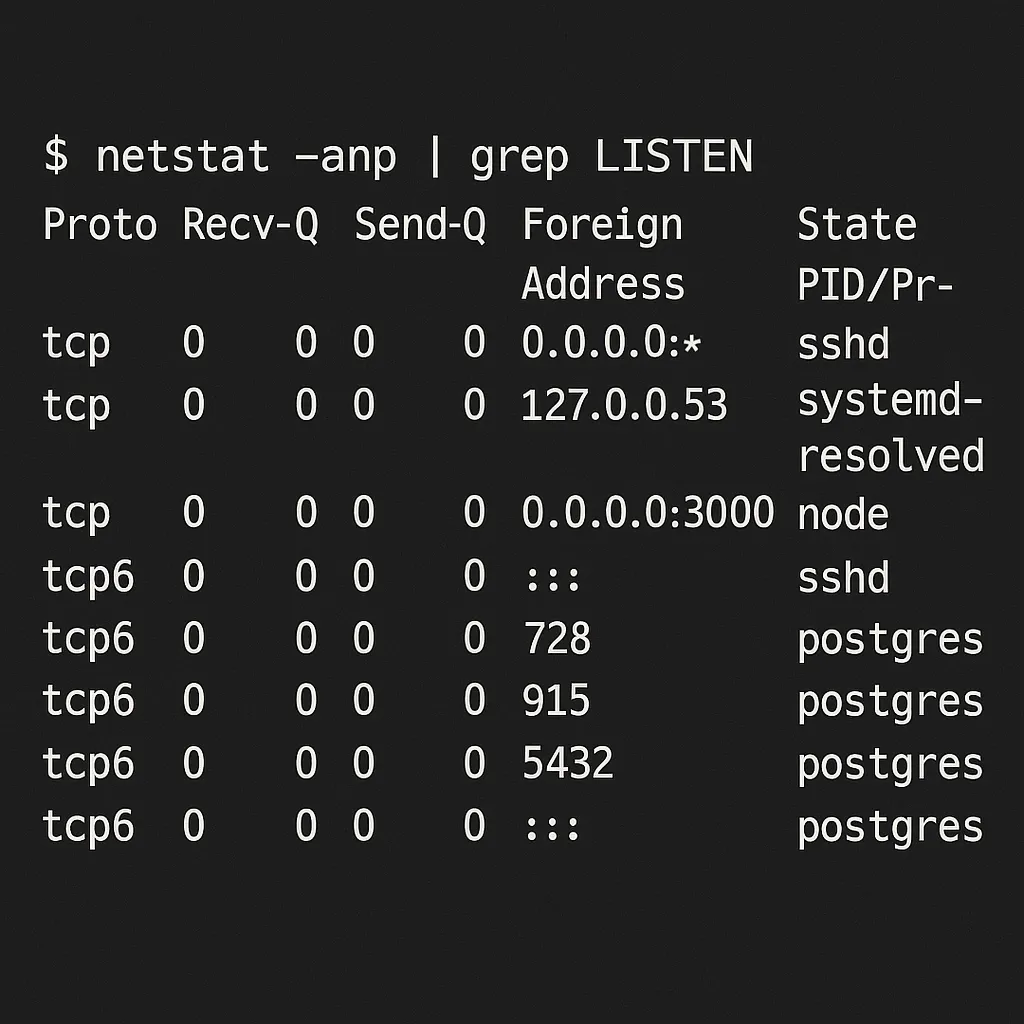
-
ss -anp-
ssstands for “socket statistics.” -
Output is often faster and more comprehensive than netstat.
-
Takes the same flags (
-a,-n,-p) for the same basic functionality.
-
Example usage:
# Using ss
ss -anp | grep LISTEN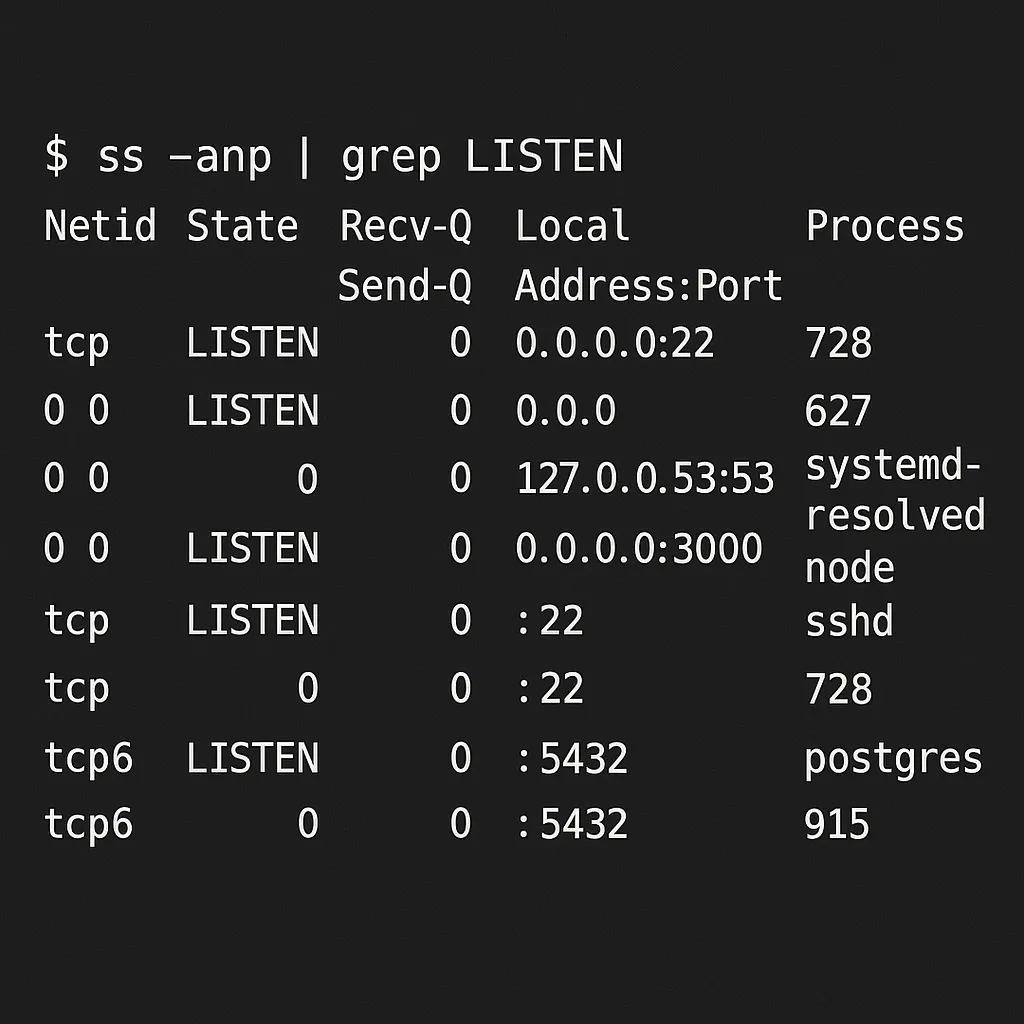
Both commands will show listening sockets along with the associated processes and PIDs.
3.2 Mapping Processes to Open Sockets
If you want to see which process is using a particular port (e.g., port 80):
ss -anp | grep ":80 "The output might look like:
LISTEN 0 128 0.0.0.0:80 0.0.0.0:* users:(("apache2",pid=1234,fd=4))This tells you:
-
The socket is in LISTEN state.
-
It’s associated with apache2, PID 1234.
Mapping processes to open sockets helps you confirm legitimate services (like web servers) or identify suspicious ones. During a pentest, you might discover an odd process name or a known malicious binary that has bound itself to a high-numbered port.
3.3 Identifying Suspicious Processes
When scanning through your socket list, keep an eye out for:
-
Unusual Port Usage: Legitimate services typically use well-known ports (e.g., 80, 443, 22). Malware or unauthorized services might run on obscure ports or high-numbered ports.
-
Unrecognized Binaries: If you see a binary name like
xyz_procthat you don’t recognize, investigate further. It might be normal or might be malicious. -
Strange Connection Destinations: Look at foreign addresses in the
ssornetstatoutput. Unfamiliar IP addresses in suspicious locations might indicate data exfiltration or a remote shell connection.
4. Real-World Examples
The best way to solidify your understanding of sockets is by walking through real-world scenarios.
4.1 Web Server and Multiple Client Connections
Scenario: A web server (e.g., Apache, Nginx) listening on port 80 (HTTP) or 443 (HTTPS).
-
Server Starts: The web server sets up a listening socket on port 80/443.
-
Client Connection: A client (e.g., a user’s browser) sends a SYN packet to the server’s IP and the target port (80 or 443).
-
Server Accepts: The server accepts the connection. A new socket is created for this specific client. Meanwhile, the original listening socket remains active to accept new clients.
-
Parallel Connections: Each connected client has its own socket. This allows the server to handle many connections simultaneously, often by passing each connection to a worker process or thread.
Pentesting Angle
-
Enumeration: Use tools like
nmapto see if the server is open on 80/443, and possibly do version detection to find vulnerabilities. -
Analysis: If you suspect malicious users or bots, you might check the server logs to see connections from suspicious IPs. On the server side,
ss -anphelps track real-time connections and might reveal suspicious processes or ephemeral ports.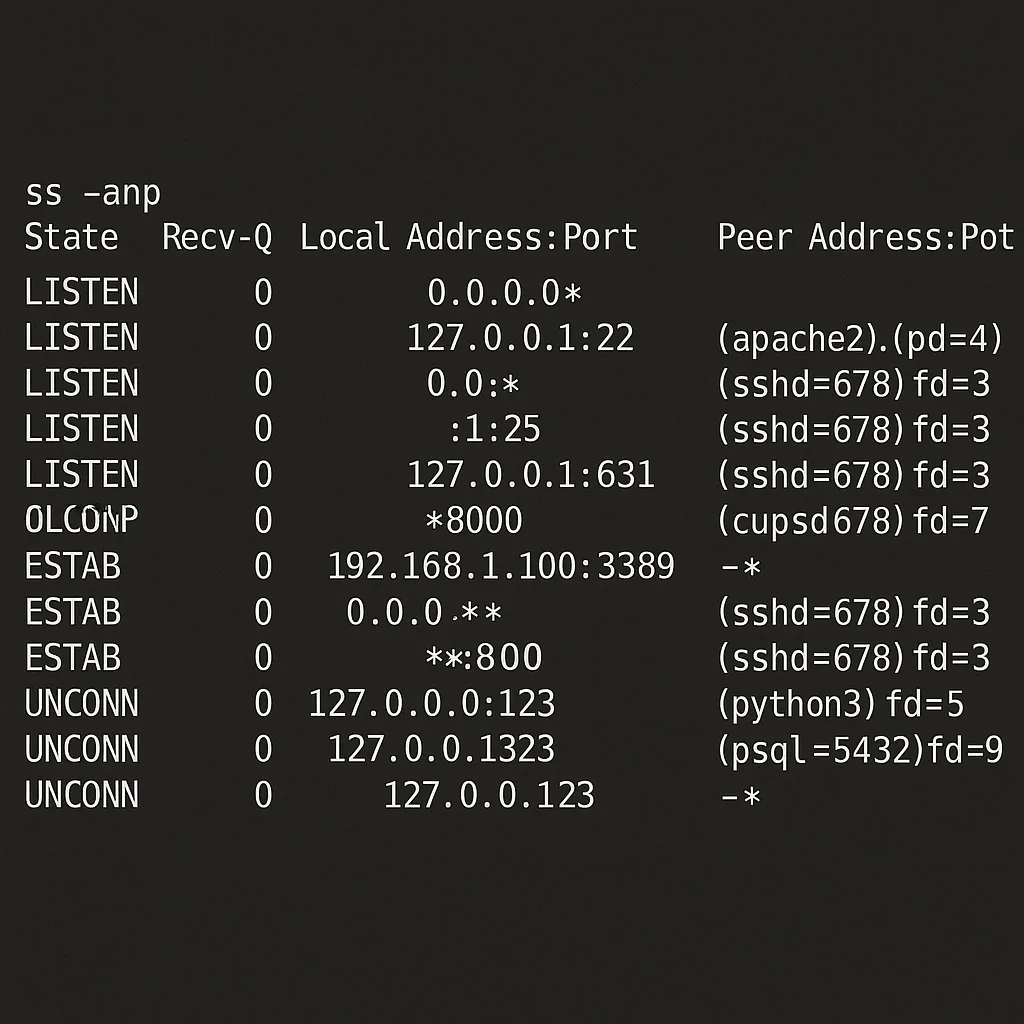
4.2 Tracing Process Communication in a Pentest
Scenario: You have compromised a machine and want to pivot or gather information about ongoing communications.
-
List Active Sockets: Use
ss -anpto list everything. -
Identify Key Processes: If you see a suspicious process named
malwareorbind_shelllistening on port 4444, that might be a reverse shell or bind shell used by the attacker. -
Investigate Connections: If the remote endpoint is an external IP, you can attempt to identify it via
whois, or see if it’s part of a known malicious block. -
Monitor Traffic: Tools like
tcpdumpor Wireshark can capture packets for deeper inspection. -
Create a Timeline: Combine logs (e.g.,
/var/log/auth.log) with netstat/ss data to figure out when the malicious process started, how it got launched, and whether it communicates with other compromised systems on the local network.
In a pentest, demonstrating that you can map out the victim’s environment and identify rogue processes is crucial. Knowing how to read socket usage is often one of the first steps in network enumeration and lateral movement.
5. Suggested Learning Path
Mastering sockets and IPC is a journey. Below is a recommended path for those looking to dive deeper, especially from a pentester’s perspective:
-
Foundations of Linux
- Familiarize yourself with the Linux file system, process management, and basic networking commands (
ls,ps,kill,ifconfigorip, etc.).
- Familiarize yourself with the Linux file system, process management, and basic networking commands (
-
Basic Networking
-
Learn about TCP/IP, the OSI model, subnetting, and basic routing.
-
Practice using
ping,curl,wget, andtelnetto understand how different protocols work.
-
-
Hands-On with netstat/ss
-
Regularly check active connections on your own machine.
-
See which processes correspond to which ports.
-
Use
ss -tlnp(TCP listening) andss -ulnp(UDP listening) to zero in on TCP or UDP.
-
-
Small Scripting Projects
-
Write simple shell scripts to parse netstat/ss output. For instance, a script that alerts you whenever a new listening port appears.
-
Experiment with
nc(netcat) to create your own mini client-server communications. You can simulate real-life scenarios like a reverse shell or a simple chat server.
-
-
Unix Domain Socket Exploration
-
Check which processes are using Unix domain sockets by running
ss -xanp. -
Interact with local services that use Unix domain sockets (e.g., MySQL can run on a socket like
/var/run/mysqld/mysqld.sock).
-
-
Practical Pentesting Labs
-
Use intentionally vulnerable virtual machines (e.g., Metasploitable2, DVWA) to practice.
-
Exploit known vulnerabilities and then inspect the resulting shell or process connections using netstat/ss.
-
-
Expand to Tools Like Wireshark & tcpdump
- Monitor traffic on an interface (
tcpdump -i eth0) and filter for suspicious traffic.
- Capture packets and analyze them in Wireshark to see details of TCP/UDP flows.
- Monitor traffic on an interface (
-
Advanced Topics
-
Investigate specialized protocols (e.g., SCTP) or container-based networking.
-
Delve into kernel-level network analysis for deeper OS-level penetration testing techniques.
-
Conclusion
Understanding how processes communicate via sockets is at the heart of both system administration and penetration testing. Whether it’s debugging why a web service is offline or tracking down a rogue backdoor that’s been installed on a target, the ability to observe and manipulate socket connections will serve you well.
-
Key Takeaways:
-
TCP provides reliable, connection-oriented communication.
-
UDP offers faster, connectionless datagrams but lacks guarantees.
-
Unix domain sockets keep communications local and efficient.
-
netstatandssare essential utilities for mapping processes to connections. -
Real-world pentesting requires understanding how services (like web servers) manage multiple client sockets and how malicious processes can hide among legitimate ones.
-
By mastering these concepts and continuously practicing in real or lab environments, you’ll gain the expertise needed to handle network-based investigations confidently. Keep exploring new challenges, set up your own labs, and experiment with tools like Wireshark, tcpdump, netcat, and scripting languages (like Bash or Python) to automate tasks. With consistent effort, you’ll soon find yourself comfortable tracing sockets in any Linux environment and uncovering potential security holes before attackers do.
Test Your Knowledge
Which of the following protocols is connection-oriented and ensures reliable data transmission?
What does the following command do? "ss -anp | grep LISTEN"
Which statement best describes Unix Domain Sockets?
During a pentest, you find a process named "xyz_proc" listening on port 4444 with "ss -anp". What is your most logical first step?
You are tracing a suspected backdoor running on a compromised Linux machine. You notice that the process is not bound to an IP address but appears in the socket list like this: " LISTEN 0 128 /tmp/.malicious.sock users:(("badproc",pid=4321,fd=3)) " What kind of socket is this most likely using?