Introduction to Basic Security Concepts
Why these concepts matter! When you sit down to run nmap, fire up Burp, or craft a payload in sqlmap, you’re stepping into a conversation that attackers have been having with defenders for decades. Every tool, every exploit, every blue-team control is really just a manifestation of three foundational ideas:
-
Who is coming after the system? – threat actors
-
How are they going to wiggle in? – attack vectors
-
What happens if they succeed? – risk & impact
If you understand those ideas deeply, learning new tools and techniques becomes an exercise in “plug and play” rather than memorisation. Let’s build that foundation, module by module, with a pentester’s lens.
1. Understanding Threat Actors
1.1 Types of Threat Actors
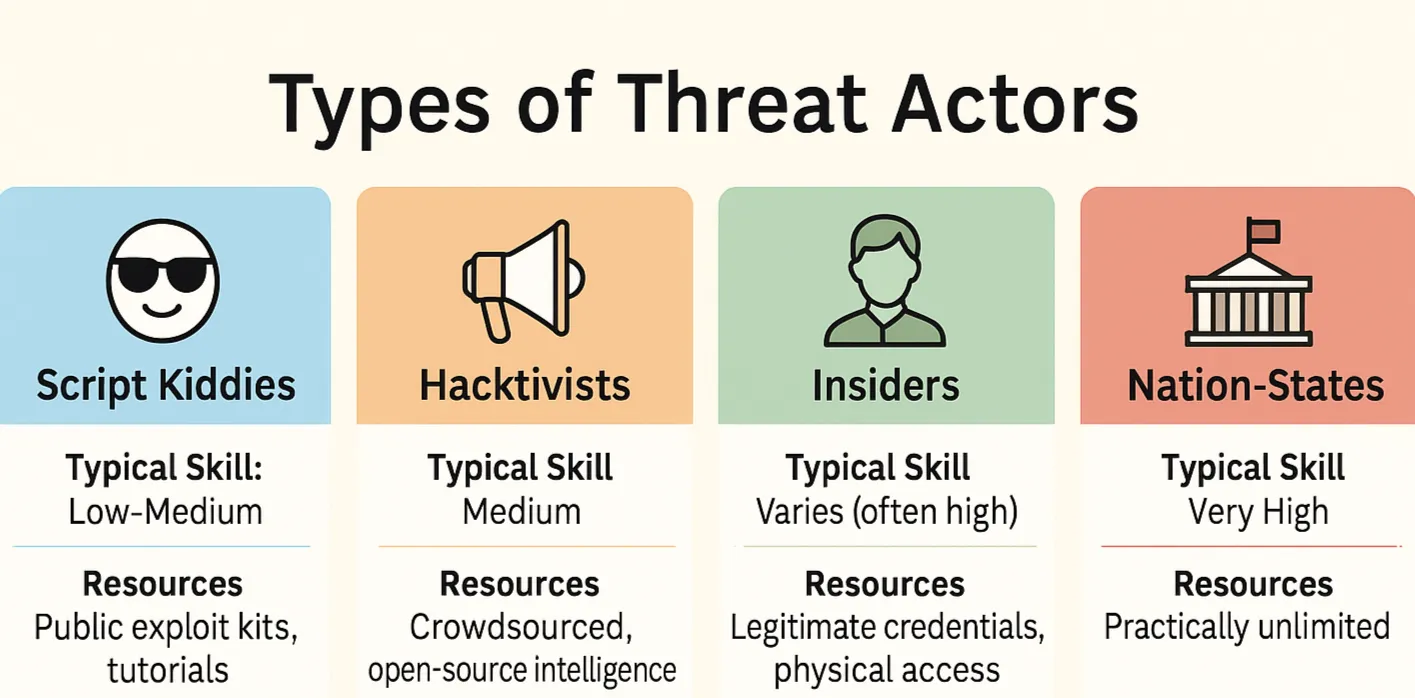
| Actor | Typical Skill | Resources | Real-World Example | Pentester Take-Away |
|---|---|---|---|---|
| Script Kiddies | Low–medium | Public exploit kits, YouTube tutorials | Mirai botnet operators age 13–15 | Your default baseline – never assume the attacker is skilled; assume they have patience and copy-paste. |
| Hacktivists | Medium | Crowdsourced, open-source intelligence | Anonymous targeting the Church of Scientology | They care about message over money. Expect defacements or data dumps, not stealth. |
| Insiders | Varies (often high) | Legitimate credentials, physical access | Sysadmin Edward Snowden exfiltrating NSA docs | Least-privilege, monitoring, & “two-person rule” beat any firewall here. |
| Nation–States | Very high | Practically unlimited | Stuxnet (US/Israel vs. Iranian centrifuges) | Assume zero-days and long dwell time; focus on detection & rapid response. |
Mnemonic: Kids yell, activists protest, insiders already live inside, and states play the long game.
Motivations in one sentence each
-
Financial gain – ransomware, card-skimming, crypto-jacking.
-
Espionage – intellectual-property theft, stealthy surveillance.
-
Political / Ideological – disruption, reputation damage, “naming and shaming.”
1.2 Risk & Impact
A pentester’s job is not to shout “I popped root!” and walk away—it’s to map that exploit to CIA:
-
Confidentiality – Could an attacker see what they shouldn’t? (e.g., patient records)
-
Integrity – Could they change anything? (e.g., stock prices, source code)
-
Availability – Could they stop the service from working? (e.g., DDoS)
Exercise (on paper): Pick any university system (learning-management, email, dorm Wi-Fi) and, for each threat-actor type above, write one sentence on how they might compromise CIA. Doing this trains your “adversary mind-set” muscle.
2. Basic Attack Vectors
2.1 Phishing
Phishing is social engineering + delivery vehicle. Ninety-plus percent of breaches still start with an email because humans click faster than IDS rules update.
Anatomy of a typical phishing email
From: [email protected]
Subject: Urgent – Password Expiry
Body: Dear Student,
Your password expires TODAY. Click here to keep access.
[malicious link]| Indicator | Why it’s Fisher-Price-easy to miss |
|---|---|
| Slight misspellings (un1versity) | Many fonts make “1” look like “l”. |
| “Urgent” language | Humans shortcut critical thinking. |
| HTTPS padlock | Phishers also buy TLS certificates. |
Preventive Measures (Pentester’s viewpoint)
-
User training with real-world simulations – Services like GoPhish let you craft campaigns; weekly drills build click-resilience.
-
Email-gateway filtering – DKIM, SPF, DMARC reduce spoofing; sandbox attachments.
-
“Report Phish” button – Shortens detection-to-response time; your red-team tests are only useful if blue-team sees the alert.
Lab idea: Spin up GoPhish in a VM, craft a campaign that triggers a credential-harvest page running on a local Docker container. Analyse which classmates click and why (with consent).
2.2 Malware
Malware = malicious + software. Think of it as the attacker’s Swiss Army knife, dropped onto the victim box.
Common Species
| Species | Defining Trait | One-line Demo for Your Lab |
|---|---|---|
| Worm | Self-replicates over network | Run Metasploit’s ms08_067_netapi in isolated subnet. |
| Trojan | Disguises as legit software | Build a fake “free-PDF-merger.exe” that opens calc.exe & a reverse shell. |
| Ransomware | Encrypts data for payment | Use minikatz & edr evasion to simulate domain-wide share encryption (NEVER on production!). |
Delivery & Infection Vectors
-
Email attachments (.docm macros)
-
Drive-by downloads (watering-hole sites exploiting browser CVEs)
-
USB drop (classic “parking-lot thumb-drive”)
Defences & Best Practices
-
Least-privilege on endpoints – Malware running as non-admin often fizzles.
-
Application whitelisting (AppLocker, WDAC) – Allows only signed/approved binaries.
-
EDR with behavioural analytics – Detects unusual PowerShell, lateral movement.
-
Regular backups + offline copy – Only reliable ransomware recovery.
Mini-blue-team drill: Load the Sysinternals Process Monitor tool, infect a sacrificial VM with the Eicar test virus, and observe registry/file touches in real time. Then craft a PowerShell Defender rule to quarantine it.
2.3 SQL Injection (SQLi)
SQLi is the OG web vulnerability (discovered 1998) and still in OWASP Top 10. Why? Because it turns poor input validation into straight-to-database remote code.
One-Slide Explanation
GET /product?id=10 → SELECT * FROM products WHERE id='10';
GET /product?id=10' OR '1'='1 → SELECT * FROM products WHERE id='10' OR '1'='1';The database happily returns all rows because '1'='1' is always true.
Pentester Workflow
-
Recon – Identify parameters reflected in SQL-like responses (
?id=?category=). -
Probe – Inject
',"and watch for 500 errors or quoting anomalies. -
Exploit – Use
UNION SELECTto dump tables or; DROP TABLE users; --for destructive proof-of-concept (never in production). -
Escalate – If MySQL root or MSSQL xp_cmdshell is available, pivot to OS.
Detection & Mitigation
-
Parameterized queries / prepared statements – Bind variables instead of concatenating strings.
-
Input sanitisation + allow-lists – Only permit characters that the business logic truly needs.
-
Least-privilege DB accounts – Web app should read-only what it must.
-
Web Application Firewall (WAF) – ModSecurity core rule set blocks common payloads; great for legacy apps while code is being fixed.
Hands-on practice:
Deploy DVWA (Damn Vulnerable Web App) in Docker.
Set SQLi challenge to “Medium.”
Use Burp Repeater and
sqlmapto enumerate database names, then craft one manual payload that exfiltrates only the
3. Suggested Learning Path (Action Plan)
“Crawl – Walk – Run” is the mantra. Master the concepts, then the tooling.
-
Week 1–2 | Threat Actors (Module 1)
-
Daily reading: One breach report (e.g., Verizon DBIR summaries).
-
Exercise: Map each breach to actor type and motivation in a notebook.
-
Outcome: You can look at a headline and instantly say “This smells like insider for financial gain.”
-
-
Week 3–4 | Attack Vectors Fundamentals (Module 2)
-
Build a small lab: two VMs (Kali & Windows10) + one LAMP server (DVWA).
-
Phishing drill – Set up GoPhish, send “password expiry” mail to yourself, capture credentials, analyse headers.
-
Malware drill – Craft a harmless reverse shell with
msfvenom, detonate on sandbox, watch Defender logs. -
SQLi drill – Dump
userstable from DVWA usingsqlmap, then patch code with prepared statements to prove the fix.
-
-
Week 5+ | Layering & Automation
-
Learn Burp Suite extensions, Python scripting for repetitive tasks, and Jupyter Notebooks for reporting.
-
Join a CTF (TryHackMe “Phishing” room, HackTheBox “Fortune”) to reinforce skills in a gamified setting.
-
-
Ongoing | Soft Skills & Ethics
-
Write post-exploitation reports in clear English—boards pay attention here.
-
Keep a personal “Indicators of Compromise (IOC)” cheat-sheet; update after every lab.
-
Read the OffSec Code of Ethics; practise minimum necessary force in every engagement.
-
4. Pro Tips from the Field
-
Think like a story-teller. Every pentest report should read: Actor → Vector → Impact → Fix.
-
Exploit and patch. After popping SQLi, spend an hour inserting parameterized queries; you’ll learn secure coding fast.
-
Automate the boring 80 %. Use bash loops or Python to enumerate 1,000 URLs for
' OR '1'='1rather than clicking each. -
Stay curious, not reckless. Never test on a system you don’t own or have written permission to hit. University disciplinary boards move faster than attackers.
-
Log everything. Terminal session recording (
scriptcommand) makes report screenshots effortless and reproducible.
5. Quick Reference Cheat-Sheet
| Vector | One-liner Test | Fix in 5 words |
|---|---|---|
| Phish | Hover over link, spot mismatch | Train, filter, MFA, report |
| Malware | Hash unknown .exe, check VT | Principle of least privilege |
| SQLi | Add ' to parameter, see error | Prepared statements 4-ever |
Print that, tape it to your monitor—field-tested reminder.
Closing Thoughts
Yes, pentesting involves cool exploits and CTF flags, but clarity of the fundamentals is what separates a “button-clicker” from a trusted security consultant. Spend focused time on threat actors and their favoured vectors, set up safe labs, document everything, and iterate. By the time you move to intermediate topics (XSS, privilege escalation, cloud hacking), you’ll find they’re just new dialects of the same language you started learning here.
Happy hacking—legally, ethically, and always with permission!
Test Your Knowledge
What would this input likely do in a vulnerable SQLi field? "1' OR '1'='1"
A hacker embeds a reverse shell inside a fake “PDF converter” tool. What type of malware is this?
A university deploys a Web Application Firewall (WAF). What is its main purpose?
What is the most appropriate way to simulate a malware infection safely in a lab?
What’s the MOST critical element of a pentest report when describing an SQLi finding?