CIA Triad and AAA
1. Introduction to the CIA Triad
Definition and Overview of Confidentiality, Integrity, Availability
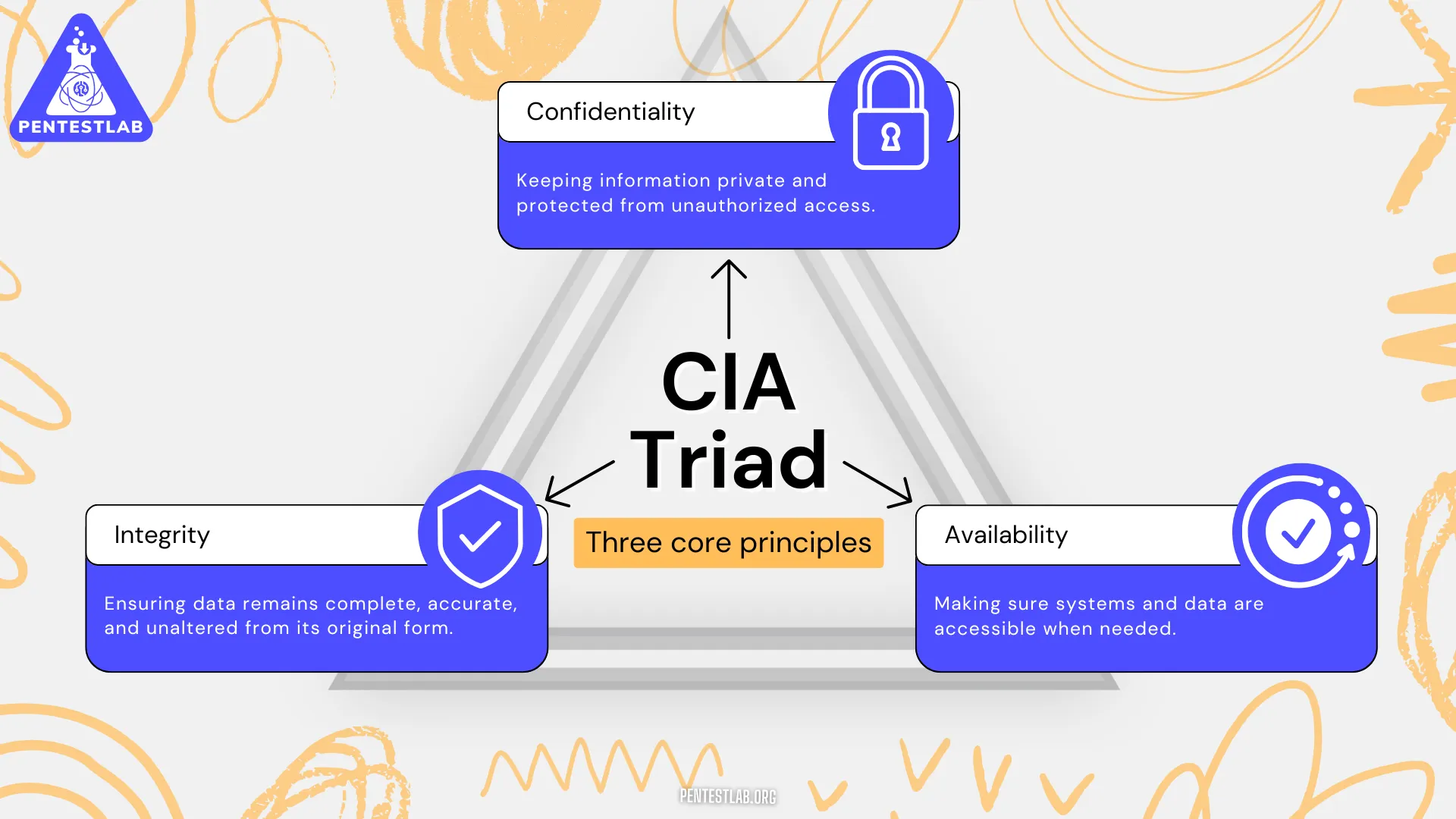
The CIA Triad forms the cornerstone of cybersecurity, consisting of three fundamental principles:
- Confidentiality – Ensuring that information is accessible only to those authorized to view it.
- Integrity – Maintaining the accuracy and consistency of data throughout its lifecycle.
- Availability – Making sure systems and data are accessible to authorized users when needed.
In any pentesting or cybersecurity effort, these three principles serve as guiding objectives. You’ll evaluate vulnerabilities, recommend mitigations, and suggest improvements that help maintain or restore these core security pillars.
Historical Context and Why the CIA Triad Is Fundamental to Cybersecurity
Cybersecurity wasn’t always as complex as it is today. In the early days of computing, protection often focused on basic physical security (e.g., locking computer rooms) and simple password mechanisms. However, as systems became networked and data transmissions increased, threats evolved rapidly. The need to protect critical information from breaches, data corruption, and service disruption led to the formalization of these three core principles.
Professionals across the globe adopted the CIA Triad because it offers a concise, universal language for identifying and discussing security needs. Whether an organization is a small startup or a multinational corporation, these three tenets remain relevant because practically every security threat targets at least one part of the Triad.
Real-World Examples of Each Component
- Confidentiality Example: A financial institution storing clients’ credit card details must ensure nobody except authorized personnel can see or manipulate these details. Encryption of data in transit (using TLS/SSL) and at rest (using disk encryption) often plays a key role here.
- Integrity Example: When an online retailer processes an order, data like product details, prices, and shipping addresses must remain accurate. Even a small manipulation—say, dropping the price from $100 to $1—compromises integrity, and can cause financial losses and legal repercussions.
- Availability Example: A streaming service must remain online for millions of users daily. If the service is taken down by a Denial-of-Service (DoS) attack, the business loses revenue, and customers get frustrated. Building redundancy and contingency plans helps maintain availability.
2. Confidentiality
Importance of Data Privacy
Confidentiality is synonymous with privacy, which is crucial not just for personal data (e.g., health records, financial information) but also for intellectual property and other business assets. In the context of penetration testing, you often probe how well an organization keeps sensitive information hidden from unauthorized access. Even a minor leak can have huge repercussions, such as reputational damage or hefty legal fines.
Methods for Ensuring Confidentiality
- Encryption: Transforming data into unreadable ciphertext unless the user has the proper decryption key. As a pentester, you’ll test whether encryption keys are stored securely, and if strong algorithms like AES are used.
- Access Controls: Ensuring proper user privileges. Role-Based Access Control (RBAC) or Mandatory Access Control (MAC) systematically enforces who can see what.
- Physical Security: Locks on server rooms, restricted data center access, CCTV monitoring, and similar safeguards that reduce the chance of an intruder physically retrieving data.
- Network Segmentation: Splitting the network into smaller segments (e.g., VLANs) so that if one segment is compromised, it doesn’t automatically give access to the entire infrastructure.
Common Threats to Confidentiality
- Eavesdropping: Attackers intercept data in transit, for instance using packet sniffers or man-in-the-middle (MITM) techniques.
- Unauthorized Access: Weak or stolen credentials allow intruders to impersonate legitimate users.
- Insider Threats: Disgruntled or careless employees leaking data.
- Phishing: Social engineering tactics trick users into giving up confidential data or credentials.
3. Integrity
Definition of Data Integrity
Data integrity ensures that information remains correct, consistent, and trustworthy from creation to consumption. Any unauthorized alteration—whether accidental or intentional—violates integrity. In pentesting, you’ll test if it’s possible for an attacker to modify data as it travels across the network or while stored in databases and file systems.
Techniques for Maintaining Integrity
- Hashing: Converting data into a fixed-length digest via algorithms such as SHA-256. If even a single bit changes, the resulting hash drastically differs from the original.
- Checksums: A simpler form of data verification often used for file downloads.
- Digital Signatures: Combining hashing with public/private key cryptography to verify that a sender is genuine and the data is unaltered.
- Version Control: Keeping track of changes in code or documents to quickly identify unauthorized modifications.
Attack Scenarios that Compromise Integrity
- Data Tampering: An attacker modifies database entries, possibly changing money transfers or forging medical records.
- Man-in-the-Middle Attacks: Hackers intercept and alter data packets in real-time, often in insecure network environments.
- Unauthorized Database Access: Exploiting SQL injection or misconfigurations to edit or delete records.
4. Availability
Ensuring Reliable Access to Systems and Data
Availability focuses on preventing disruptions to services and networks. In a pentesting scenario, you might evaluate load balancing, redundancy setups, and how quickly a system can recover from outages.
Techniques for High Availability
- Redundancy: Duplicate critical components (servers, routers, power supplies) so that a single point of failure doesn’t bring the entire system down.
- Failover Systems: Automatic switching to a backup if the primary system fails.
- Regular Backups: Storing data offsite or in the cloud for quick restoration if a system is compromised or data is lost.
- Disaster Recovery (DR) Planning: Detailed procedures for how to get systems running again after catastrophic failures (e.g., natural disasters, massive cyberattacks).
Common Denial-of-Service (DoS) and Distributed Denial-of-Service (DDoS) Threats
- Flood Attacks: Attackers overwhelm a target with a massive volume of traffic, making legitimate requests impossible to service.
- Application-Layer Attacks: Attackers repeatedly access resource-intensive endpoints to exhaust a service’s CPU or memory.
- Botnets: Attackers compromise numerous devices (zombies) and coordinate them to direct traffic at a single target, amplifying the effect.
5. AAA (Authentication, Authorization, Accounting)
Definitions and Roles of Authentication, Authorization, and Accounting
The AAA framework complements the CIA Triad by focusing on how users and devices prove their identity, get permission for specific activities, and log those activities.
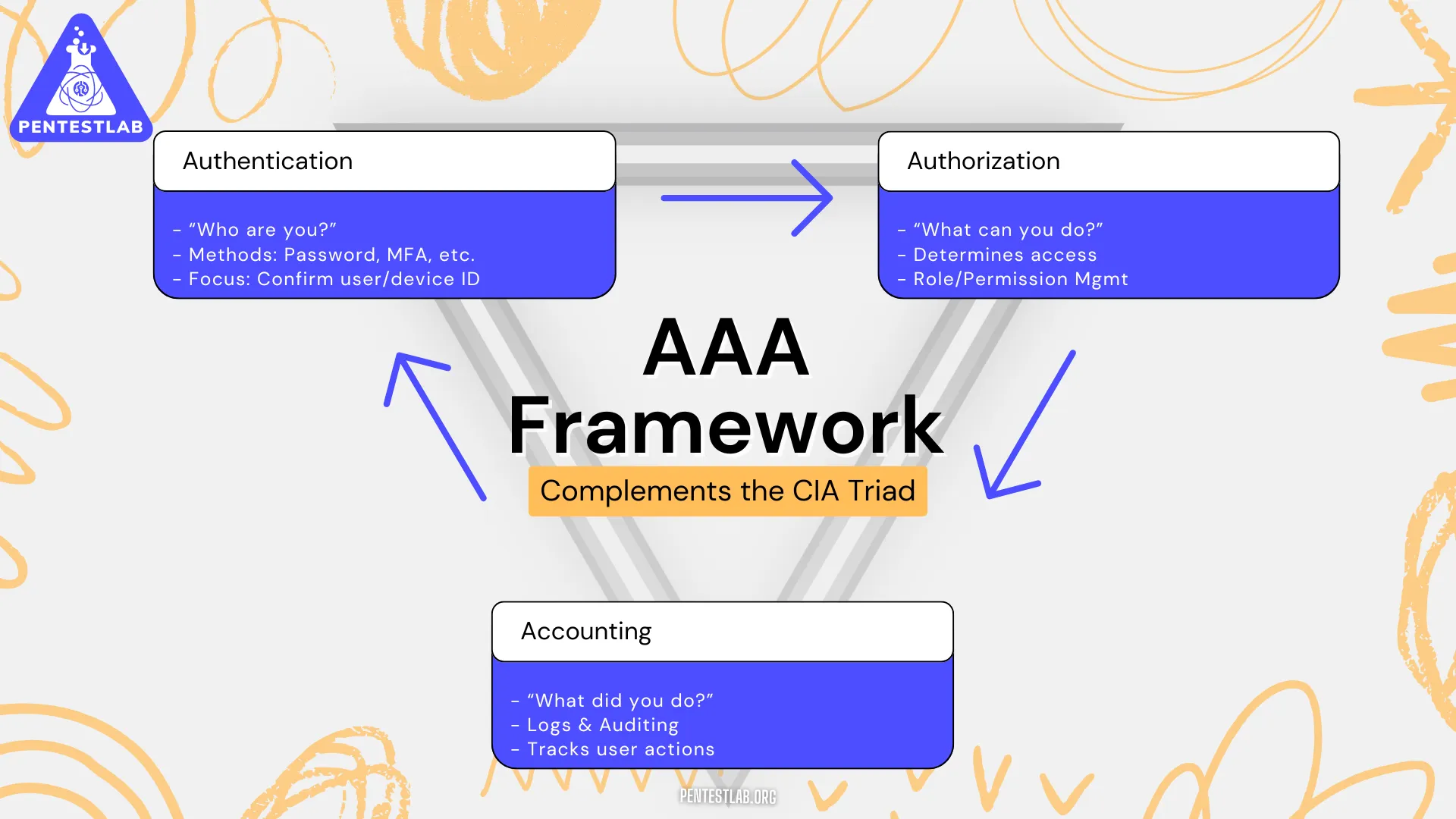
- Authentication: Verifying the identity of a user or device before granting access. Common methods include passwords, biometrics, and multi-factor authentication (MFA). In pentesting, you’ll examine login flows to find weaknesses in how credentials are verified.
- Authorization: Determining what an authenticated entity is allowed to do. For example, once a user logs in, can they view HR records, change system settings, or access financial data? Proper role and permission management is crucial here.
- Accounting: Tracking and logging actions performed by the user or system. This ensures there is an audit trail which can be reviewed for compliance, and helps identify suspicious activities.
How AAA Relates to the CIA Triad
- Confidentiality: Proper authentication and authorization ensure only the correct people can see confidential data.
- Integrity: Thorough logging and oversight of changes help identify or prevent tampering.
- Availability: Well-designed authentication systems and usage logs can mitigate attacks that might disrupt legitimate user access. For instance, if your logs show repeated failed login attempts from a specific IP, you can quickly block that IP to maintain service availability for other users.
Tools and Protocols for AAA
- RADIUS (Remote Authentication Dial-In User Service): A protocol commonly used to manage network access. It centralizes AAA for users. In penetration testing, you might test whether the RADIUS implementation is configured securely.
- TACACS+ (Terminal Access Controller Access-Control System Plus): Similar in purpose to RADIUS, but separates out the authentication, authorization, and accounting functions for more granular control.
- LDAP (Lightweight Directory Access Protocol): Used for accessing and managing directory services, often in Microsoft Active Directory environments.
- Kerberos: A network authentication protocol that uses tickets to authenticate user identities without sending passwords across the network repeatedly.
Applying the Concepts as a Pentester
By understanding the CIA Triad and AAA, you gain a framework to approach any new environment or project. Here’s how you might apply this knowledge in a real-world pentest:
- Planning and Scoping: Identify which parts of the target environment store sensitive data and which systems are most critical for operations.
- Threat Modeling: Consider how an attacker might compromise confidentiality (e.g., targeting unencrypted data), integrity (e.g., tampering with records), or availability (e.g., launching a DDoS).
- Vulnerability Identification: Probe authentication mechanisms (part of AAA) to see if they’re vulnerable to brute-force attacks, check for injection flaws that might compromise data integrity, and look for misconfigurations that could expose data to unauthorized users.
- Exploitation: Attempt to exploit identified weaknesses in a controlled environment. You might try to escalate privileges (authorization issue) or intercept and modify data in transit (integrity issue).
- Reporting: Finally, document vulnerabilities in the context of CIA Triad impact. For instance, show how a discovered SQL injection risk can lead to data theft (confidentiality breach) or data tampering (integrity breach). Propose measures like stronger encryption, robust password policies, improved network segmentation, or multi-factor authentication to address these gaps.
Conclusion
Understanding the CIA Triad and AAA is a critical step in your journey as a pentester. The CIA Triad—Confidentiality, Integrity, Availability—anchors every security discussion, ensuring you know what you’re protecting and why. AAA—Authentication, Authorization, Accounting—provides a systematic approach to controlling and monitoring access. Together, they shape how you view threats, design defenses, and conduct penetration tests in a methodical, outcome-focused way.
Always keep these principles at the forefront of your mind. As you gain practical experience, map every security tool, policy, and procedure you encounter back to these core concepts. This mind-set will help you not only spot potential weaknesses but also suggest the right combinations of technical and administrative safeguards to protect organizations effectively.
By continuously practicing and applying the concepts outlined above, you’ll develop the proficiency needed to excel in any cybersecurity role, particularly in penetration testing. Good luck on your learning journey!
Test Your Knowledge
Which principle of the CIA Triad ensures that information is only accessible to those authorized to view it?
Which AAA component is responsible for verifying the identity of a user before granting access?
Which of the following is a common technique used to maintain data integrity?
Which of the following strategies helps ensure availability by automatically distributing incoming network traffic across multiple servers or resources?
Which protocol is commonly associated with AAA and separates the authentication and authorization functions, providing more granular control over command-level access?